File list
From The ECRYPT Hash Function Website
This special page shows all uploaded files.
| Date | Name | Thumbnail | Size | Description | Versions |
|---|---|---|---|---|---|
| 11:28, 20 July 2010 | Ramakers Narinx2010ECHO-Hamsi-Luffa Thesis DUTCH.pdf (file) | 5.58 MB | Full thesis in Dutch sent by Wim Ramakers on July 10, 2010 with request to be hosted on SHA-3 webpage. | 1 | |
| 11:27, 20 July 2010 | Ramakers Narinx2010ECHO-Hamsi-Luffa ExtendedAbstract ENGLISH.pdf (file) | 3.16 MB | Extended abstract in English sent by Wim Ramakers on July 10, 2010 with request to be hosted on SHA-3 webpage. | 1 | |
| 11:25, 21 July 2010 | Ramakers Narinx2010ECHO-Hamsi-Luffa VHDL sources.zip (file) | 1.08 MB | VHDL sources sent by Wim Ramakers on July 19, 2010 with request to be hosted on SHA-3 webpage. | 1 | |
| 12:21, 12 November 2009 | 20091112 SHA-3 HW stillich.pdf (file) | 343 KB | Presentation from September 16, 2009, updated with final round-2 tweak status and a correction in the description of JH. | 1 | |
| 08:26, 17 September 2009 | 20090916 SHA-3 HW stillich.pdf (file) | 343 KB | Presentation of SHA-3 HW results, September 16, 2009 including some updates on candidate tweaks. | 1 | |
| 10:15, 17 February 2010 | FPGA Implementation of Shabal - First Results.pdf (file) | 264 KB | Note sent by Julien Francq (Julien.Francq@eads.com) on Feb. 16, 2010. Mirrored on SHA-3 zoo page as currently there is no web link for this note. | 1 | |
| 11:47, 23 September 2009 | 20090922-2230 SHA-3 round2 tweaks.pdf (file) | 17 KB | Clarified tweak description for SIMD | 2 | |
| 20:14, 21 September 2009 | 20090921-2015 SHA-3 round2 tweaks.pdf (file) | 17 KB | Updated tweak status for SIMD. | 1 | |
| 17:28, 18 September 2009 | 20090918-1730 SHA-3 round2 tweaks.pdf (file) | 17 KB | Added tweak status for Fugue and Shabal. | 1 | |
| 12:48, 7 November 2008 | HW type ext-mem.jpg (file) | 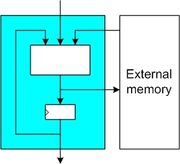 |
17 KB | 2 | |
| 11:17, 7 November 2008 | HW type self-cont.jpg (file) | 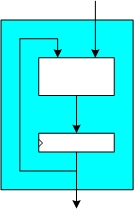 |
11 KB | Illustation of self-contained hardware implementation. | 1 |
| 22:56, 16 September 2009 | 20090916-2245 SHA-3 round2 tweaks.pdf (file) | 11 KB | SHA-3, round 2 tweak status | 1 | |
| 11:19, 7 November 2008 | HW type core-funct.jpg (file) | 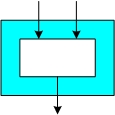 |
6 KB | Illustration of hardware implementation comprising just the core functionality of the hash. | 1 |