Difference between revisions of "SHA-1"
From The ECRYPT Hash Function Website
(→Claimed Security Margins) |
(→General Description) |
||
| Line 1: | Line 1: | ||
== General Description == | == General Description == | ||
| − | SHA-1 is an iterated hash function. | + | |
| + | SHA-1 is an iterated hash function. It can be used to | ||
| + | compute a 160-bit hash value for messages having a length of less | ||
| + | than <amsmath>$2^{64}$</amsmath> bits, cf. [http://csrc.nist.gov/publications/fips/fips180-2/fips180-2.pdf FIPS 180-2 Secure Hash Standard]. | ||
| + | As most iterated hash functions, SHA-1 applies MD strengthening. | ||
| + | |||
=== Compression Function === | === Compression Function === | ||
| − | The compression function | + | The compression function processes input message blocks of 512 bits and |
| + | produces a 160-bit chaining value. The compression function of | ||
| + | SHA-1 basically consists of two parts: the message expansion and | ||
| + | the state update transformation. The chaining variable <amsmath>$h_{i-1}$</amsmath> (''iv'' in the first iteration) is added to the output of the state update transformation (feed forward). This is graphically | ||
| + | illustrated in <!-- \nh{Figure}~\ref{fig:SHA1CompressionFunction}--!>. | ||
| + | |||
| + | [[image:SHA1CompressionFunction.png|right|thumb|250px|The SHA-1 compression function]] | ||
==== Message Expansion ==== | ==== Message Expansion ==== | ||
Revision as of 09:30, 12 October 2006
1 General Description
SHA-1 is an iterated hash function. It can be used to
compute a 160-bit hash value for messages having a length of less
than 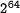 bits, cf. FIPS 180-2 Secure Hash Standard.
As most iterated hash functions, SHA-1 applies MD strengthening.
bits, cf. FIPS 180-2 Secure Hash Standard.
As most iterated hash functions, SHA-1 applies MD strengthening.
1.1 Compression Function
The compression function processes input message blocks of 512 bits and
produces a 160-bit chaining value. The compression function of
SHA-1 basically consists of two parts: the message expansion and
the state update transformation. The chaining variable 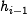 (iv in the first iteration) is added to the output of the state update transformation (feed forward). This is graphically
illustrated in
(iv in the first iteration) is added to the output of the state update transformation (feed forward). This is graphically
illustrated in