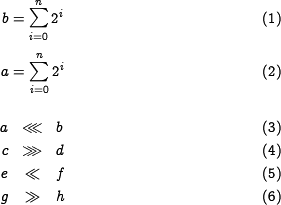Difference between revisions of "The eHash Main Page"
(→References and bibtex) |
(→Generic Attacks on Hash Functions) |
||
| Line 8: | Line 8: | ||
== Generic Attacks on Hash Functions == | == Generic Attacks on Hash Functions == | ||
| + | |||
| + | === Birthday Attack & Generalized Birthday Attack === | ||
== Some How Tos == | == Some How Tos == | ||
Revision as of 16:46, 24 October 2006
Contents
1 List of Hash Functions
On this page you can find a collection of existing hash functions.
Collection of Cryptographic Hash Functions
2 Notation and Definition
3 Generic Attacks on Hash Functions
3.1 Birthday Attack & Generalized Birthday Attack
4 Some How Tos
4.1 Working with maths and Tex
We can write "normal" latex equation by using the math class. For instance the following code
<math>
{\textbf x}_{t} = {\textbf f}({x}_{t-1},{u}_{t-1},{p}_{t-1})
</math>
is displayed as
<math> {\textbf x}_{t} = {\textbf f}({x}_{t-1},{u}_{t-1},{p}_{t-1}) </math>
In order to use tex commands from the amsmath package we use the class amsmath. Automated numbering of equations works within a single amsmath environment. The class amsmath uses the tex template defined in /var/www/html/mediawiki/extensions/wikitex/wikitex.math.inc.tex
I changed the template such that we can define global commands. The template looks like
\documentclass[10pt]{article}
\usepackage{amssymb,amsmath,amscd,concmath}
% we can define whatever comments we would like to use for consistency.
% of course we have to somewhere list this special commands (may be we can use
% a pop up with editiing help or somkething similar
% for instance:
\newcommand{\rs}{\ensuremath{\gg}} %right shift >>
\newcommand{\ls}{\ensuremath{\ll}} %left shift <<
\newcommand{\rr}{\ensuremath{\ggg}} %right rotate >>>
\newcommand{\lr}{\ensuremath{\lll}} %left rotate <<<
\pagestyle{empty}
\begin{document}
%value%
\end{document}
For instance:
| code fragment | displayed equation |
|---|---|
<amsmath>
\begin{equation}
a = \sum_{i=0}^{n}{2^i}
\end{equation}
</amsmath>
|
|
| %value% in tex-template is \begin{equation}...\end{equation} | |
If we start a new amsmath environment then the equation numbering starts from counter=1 again. Start a new amsmath environment:
as we see both envrionments start with 1.
Note: to refer to an equation we will have to use a wiki link ...
If we use math inline then we have the following possibilities:
- Best know attack: 263 by Wang et.al. using html:
2<sup>63</sup>
- Best know attack:
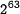 by Wang et.al. using amsmath
by Wang et.al. using amsmath <amsmath>\begin{displaymath}2^{63}\end{displaymath}</amsmath> - Best know attack: <math>2^{63}</math> by Wang et.al. using math
<math>2^{63}</math>
I think the first case looks best regarding the inline alignment. So I would suggest to use html for powers.
4.2 References and bibtex
4.2.1 Misc
<bibtex>
@MISC{HATTORI2004Complexityofthe,
author = {Mitsuhiro HATTORI and Shoichi HIROSE and Susumu YOSHIDA},
title = {Complexity of the Collision and Near-Collision Attack on SHA-0 with Different Message Schedules},
howpublished = {Cryptology ePrint Archive, Report 2004/325},
year = {2004},
note = {\url{http://eprint.iacr.org/}},
url = {http://eprint.iacr.org/},
}
</bibtex>
is displayed as:
Mitsuhiro HATTORI, Shoichi HIROSE, Susumu YOSHIDA - Complexity of the Collision and Near-Collision Attack on SHA-0 with Different Message Schedules
- ,2004
- http://eprint.iacr.org/
BibtexAuthor : Mitsuhiro HATTORI, Shoichi HIROSE, Susumu YOSHIDA
Title : Complexity of the Collision and Near-Collision Attack on SHA-0 with Different Message Schedules
In : -
Address :
Date : 2004
4.2.2 InProceedings
<bibtex>
@INPROCEEDINGS{2,
author = {Daewan Han and Sangwoo Park and Seongtaek Chee},
title = {Cryptanalysis of the Modified Version of the Hash Function Proposed at PKC'98.},
booktitle = {Fast Software Encryption 2002},
year = {2002},
series = {LNCS},
pages = {252-262},
volume = {2365},
publisher = {Springer},
editor = {Joan Daemen and Vincent Rijmen},
abstract = {This is the abstract of this paper}
}
</bibtex>
is displayed as:
Daewan Han, Sangwoo Park, Seongtaek Chee - Cryptanalysis of the Modified Version of the Hash Function Proposed at PKC'98.
- Fast Software Encryption 2002 2365:252-262,2002
- BibtexAuthor : Daewan Han, Sangwoo Park, Seongtaek Chee
Title : Cryptanalysis of the Modified Version of the Hash Function Proposed at PKC'98.
In : Fast Software Encryption 2002 -
Address :
Date : 2002
4.2.3 Article
<bibtex>
@ARTICLE{3,
author = {Hans Dobbertin},
title = {Cryptanalysis Of MD4},
journal = {Journal of Cryptology},
year = {1998},
volume = {11},
number = {4},
pages = {253--271},
}
</bibtex>
is displayed as:
Hans Dobbertin - Cryptanalysis Of MD4
- Journal of Cryptology 11(4):253--271,1998
- BibtexAuthor : Hans Dobbertin
Title : Cryptanalysis Of MD4
In : Journal of Cryptology -
Address :
Date : 1998
4.2.4 Book
<bibtex>
@BOOK{4,
title = {Handbook of Applied Cryptography},
publisher = {CRC Press},
year = {1997},
author = {Alfred J. Menezes and Paul C. van Oorschot and Scott A. Vanstone},
note = {Available online at \url{http://www.cacr.math.uwaterloo.ca/hac/}},
}
</bibtex>
is displayed as:
Alfred J. Menezes, Paul C. van Oorschot, Scott A. Vanstone - Handbook of Applied Cryptography
4.3 About different skins
Every user can define his own skin. Nevertheless, it turnes out the the skin influences the alignment of inline amsmath environments. If we use the standard skin, namely MonoBook (default) then the alignment is pretty ok.
therefore, I suggest to keep this skin as default.
5 Getting started
ECRYPT is a Network of Excellence within the Information Societies Technology (IST) Programme of the European Commission. The information on this web site is provided as is, and no guarantee or warranty is given or implied that the information is fit for any particular purpose. The user thereof uses the information at his or her sole risk and liability.