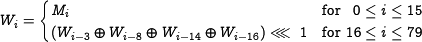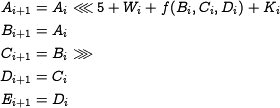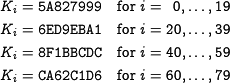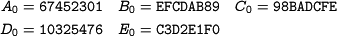Difference between revisions of "SHA-1"
(→Compression Function) |
(→Compression Function) |
||
| Line 11: | Line 11: | ||
produces a 160-bit chaining value. The compression function of | produces a 160-bit chaining value. The compression function of | ||
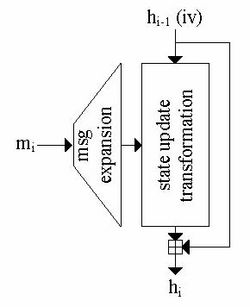
SHA-1 basically consists of two parts: the message expansion and | SHA-1 basically consists of two parts: the message expansion and | ||
| − | the state update transformation. The chaining variable <amsmath>$h_{i-1}$</amsmath> (''iv'' in the first iteration) is added to the output of the state update transformation (feed forward) | + | the state update transformation. The chaining variable <amsmath>$h_{i-1}$</amsmath> (''iv'' in the first iteration) is added to the output of the state update transformation (feed forward). |
| − | |||
[[image:SHA1CompressionFunction.jpg|right|thumb|250px|The SHA-1 compression function]] | [[image:SHA1CompressionFunction.jpg|right|thumb|250px|The SHA-1 compression function]] | ||
Revision as of 11:38, 12 October 2006
Contents
1 General Description
SHA-1 is an iterated hash function. It can be used to
compute a 160-bit hash value for messages having a length of less
than 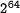 bits, cf. FIPS 180-2 Secure Hash Standard.
As most iterated hash functions, SHA-1 applies MD strengthening.
bits, cf. FIPS 180-2 Secure Hash Standard.
As most iterated hash functions, SHA-1 applies MD strengthening.
1.1 Compression Function
The compression function processes input message blocks of 512 bits and
produces a 160-bit chaining value. The compression function of
SHA-1 basically consists of two parts: the message expansion and
the state update transformation. The chaining variable 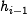 (iv in the first iteration) is added to the output of the state update transformation (feed forward).
(iv in the first iteration) is added to the output of the state update transformation (feed forward).
1.1.1 Message Expansion
The message expansion is defined as follows:
1.1.2 State Update Transformation
1.2 Padding Method
1.3 Constantsand Initial Value
1.3.1 Constants
1.3.2 Initial Value
2 Claimed/Expected Security Margins
3 Security Anaylsis
- Best know attack:
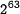 by Wang et.al.
by Wang et.al. - Best known collision example: 64-step collision by De Canniere and Rechberger
something like: best know attack to date: kind of attack, which variant has been looked at (e.g. round-reduced), complexity, and reference to paper and abstract.
may be make here a new page with the other cryptanalysis results.