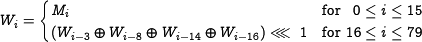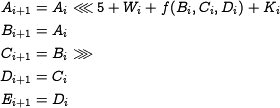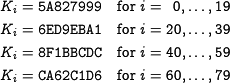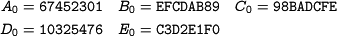Difference between revisions of "SHA-1"
From The ECRYPT Hash Function Website
(→State Update Transformation) |
|||
| Line 6: | Line 6: | ||
==== Message Expansion ==== | ==== Message Expansion ==== | ||
| + | The message expansion is defined as follows: | ||
| + | |||
| + | <amsmath> | ||
| + | \begin{equation*} | ||
| + | W_i = | ||
| + | \begin{cases} | ||
| + | M_i & \text{for $\phantom{1}0 \leq i \leq 15$} \\ | ||
| + | (W_{i-3} \oplus W_{i-8} \oplus W_{i-14} \oplus W_{i-16}) \lr\ 1 & \text{for $16 \leq i \leq 79$} | ||
| + | \end{cases} | ||
| + | \end{equation*} | ||
| + | </amsmath> | ||
| + | |||
==== State Update Transformation ==== | ==== State Update Transformation ==== | ||
| Line 21: | Line 33: | ||
=== Padding Method === | === Padding Method === | ||
| − | === Initial Value | + | === Constantsand Initial Value === |
| + | ==== Constants ==== | ||
<amsmath> | <amsmath> | ||
| − | K_i = \ | + | \begin{equation*} |
| + | \begin{aligned} | ||
| + | K_i &= \hex{5A827999} \quad \text{for $i=\phantom{0}0,\dots,19$} \\ | ||
| + | K_i &= \hex{6ED9EBA1} \quad \text{for $i=20,\dots,39$} \\ | ||
| + | K_i &= \hex{8F1BBCDC} \quad \text{for $i=40,\dots,59$} \\ | ||
| + | K_i &= \hex{CA62C1D6} \quad \text{for $i=60,\dots,79$} \\ | ||
| + | \end{aligned} | ||
| + | \end{equation*} | ||
| + | </amsmath> | ||
| + | |||
| + | ==== Initial Value ==== | ||
| + | <amsmath> | ||
| + | \begin{equation*} | ||
| + | \begin{aligned} | ||
| + | A_0 &= \hex{67452301} \quad B_0 = \hex{EFCDAB89} \quad C_0 = \hex{98BADCFE}\\ | ||
| + | D_0 &= \hex{10325476} \quad E_0 = \hex{C3D2E1F0} | ||
| + | \end{aligned} | ||
| + | \end{equation*} | ||
</amsmath> | </amsmath> | ||
| Line 31: | Line 61: | ||
== Security Anaylsis == | == Security Anaylsis == | ||
| − | * Best know attack: < | + | * Best know attack: <amsmath>\begin{displaymath}2^{63}\end{displaymath}</amsmath> by Wang et.al. |
* Best known collision example: 64-step collision by De Canniere and Rechberger | * Best known collision example: 64-step collision by De Canniere and Rechberger | ||
Revision as of 10:42, 12 October 2006
Contents
1 General Description
SHA-1 is an iterated hash function.
1.1 Compression Function
The compression function takes as input a 512-bit message block and a 160-bit chaining variable, and produces a 160-bit chaining value. The compression function is described as follows:
1.1.1 Message Expansion
The message expansion is defined as follows:
1.1.2 State Update Transformation
1.2 Padding Method
1.3 Constantsand Initial Value
1.3.1 Constants
1.3.2 Initial Value
2 Claimed Security Margins
3 Security Anaylsis
- Best know attack:
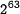 by Wang et.al.
by Wang et.al. - Best known collision example: 64-step collision by De Canniere and Rechberger
something like: best know attack to date: kind of attack, which variant has been looked at (e.g. round-reduced), complexity, and reference to paper and abstract.
may be make here a new page with the other cryptanalysis results.